LDAP Integration Module
The LDAP integration enables you to unlock FreeScout’s potential for large businesses and provide high-powered support. Module allows your LDAP users to authenticate into FreeScout. You can also import & synchronize LDAP users. The module allows your support agents to authenticate into FreeScout, customers can not be authenticated.
Features
- LDAP authentication.
- Supported LDAP servers: Microsoft Active Directory, OpenLDAP, FreeIPA. Correct work of other servers we can’t guarantee.
- Automatic fallback to local database authentication if LDAP authentication fails.
- Import and automatic synchronization of LDAP users.
- LDAP attributes mapping.
- Assigning imported users to mailboxes.
- SSO authentication.
- Detailed import logs.
Requirements
- PHP LDAP extension.
- LDAP integration is possible only if users in your LDAP database have email attribute.
- To import LDAP users they must have “person” or “inetOrgPerson” object class.
Configuration
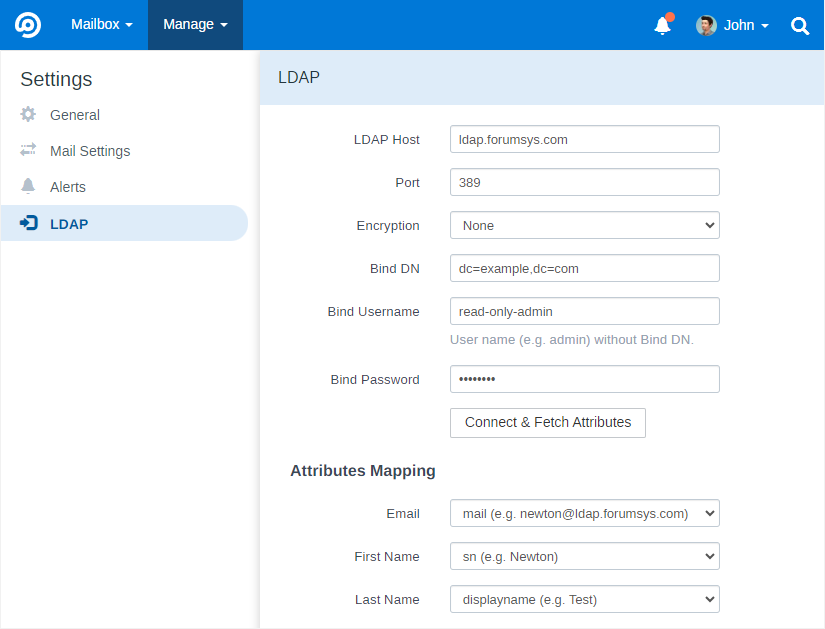
Keep in mind that “Bind DN” field must be exact DN of the Binding Username and it should NOT contain admin username.
When clicking “Connect & Fetch Attributes” the module retrieves users’ attributes from users located in “Bind DN” and “DNs and Filters” fields.
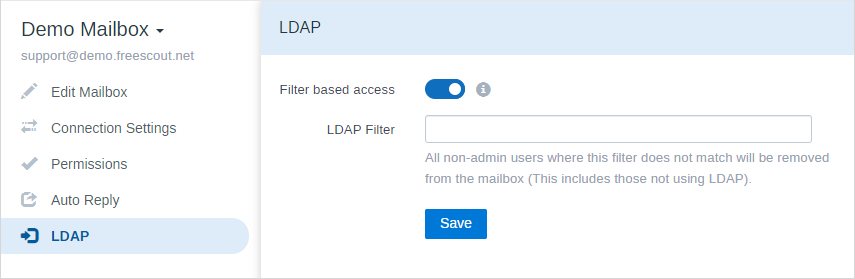
If you want users to be automatically mapped to some mailboxes, configure LDAP Filter for corresponding mailboxes. Example: (&(memberOf=cn=demo,dc=freescout,dc=net))
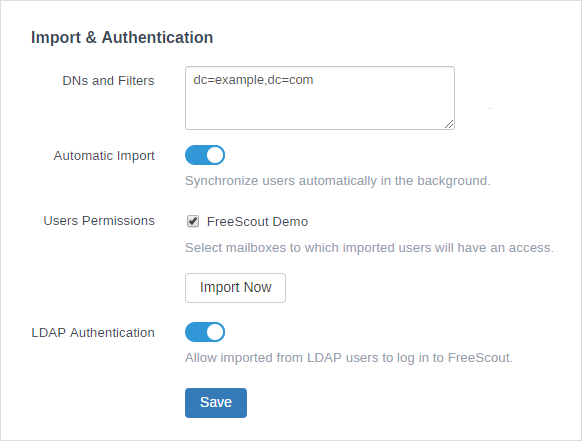
Importing Users
Users can be imported manually or automatically in the background. Users are imported from “DNs and Filters” specified in “Import & Authentication” section.
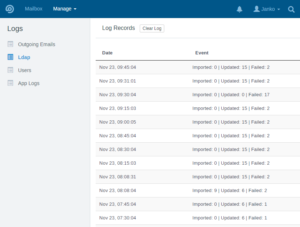
In “Manage > Logs > LDAP” importing logs can be found.
SSO Authentication
Domain users can authenticate into FreeScout automatically when they open application by the pre-populated $_SERVER[‘AUTH_USER’] (or any other) that is filled when SSO is enabled on your server. When SSO authentication is configured when you visit your site, a user account will be created (if one does not exist already) with a random password and then automatically logged in.
Microsoft Azure
This module is compatible with Microsoft Azure. Instead of using the username (sAMAccountName) to do the login, use the CN to bind. You can install Active Directory Explorer onto a joined machine and find the full DN of the user. The LDAP module sets the bind request using “CN={bind user},{Bind DN string}”
CA cert
Specify Encryption: SSL and “TLS_CACERT /etc/openldap/ca.pem” in ldap.conf and mount it to use it with Docker images:
Volumes:
– path/to/tls/ca.pem:/etc/openldap/ca.pem:ro
– path/to/ldap.conf:/etc/openldap/ldap.conf:ro
Troubleshooting
Credentials invalid
The module does not provide LDAP connection logs. If you have access to the LDAP server you should be able to see what is being queried and what is wrong in the LDAP server logs.
If you are receiving “Credentials invalid” error, make sure that “Bind DN” and “Bind Username”. “Bind DN” should NOT contain admin username. Admin username should be present ONLY in “Bind Username” – only username without without “cn=” or “uid=”. In your LDAP the admin user must be located under “Bind DN”.
I can’t log in anymore
If you can’t log in and want to disable LDAP module, remove the module from /Modules folder and clear app cache.
ldap_connect(): Could not create session handle
If you are receiving “ldap_connect(): Could not create session handle: Bad parameter to an ldap routine” error make sure that you’ve specified a proper LDAP Host: it has to be host name or IP address without protocol or port (examples: ldap.forumsys.com, 192.168.152.3).
In order to make sure that your PHP’s LDAP extension is working properly, you can try to connect to the test OpenLDAP server:
- LDAP Host: ldap.forumsys.com
- Port: 389
- Encryption: none
- Base DN: dc=example,dc=com
- Bind Username: read-only-admin
- Bind Password: password
How can I log in under an imported user
To log in under one of the imported test users enable “LDAP Authentication” option and use password as the password to log in.
After clicking Connect & Fetch attributes some attributes are missing
Set missing attributes for some user mentioned in parenthesis as a “(e.g.)” .
LDAP Filter has no effect – everyone in our LDAP system can log in
LDAP module first tries to authenticate a user against “Bind DN”, if not successful – it tries all the “DNs and Filters”. If your Bind DN is dc=example,dc=org for example all, users located in groups and units below dc=example,dc=org will be able to authenticate (for example cn=freescout,dc=example,dc=org). To avoid this you need to change your Bind DN to something like cn=admins,dc=example,dc=org and move your admin user there.
LDAP over SSL to Active Directory does not work
Add/modify the following line (see this discussion):
TLS_REQCERT never