OAuth & Social Login Module
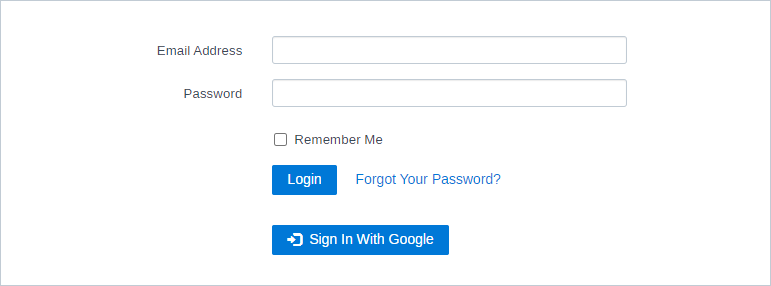
Using this module you can let your support agents login to FreeScout via any OAuth provider or social networks.
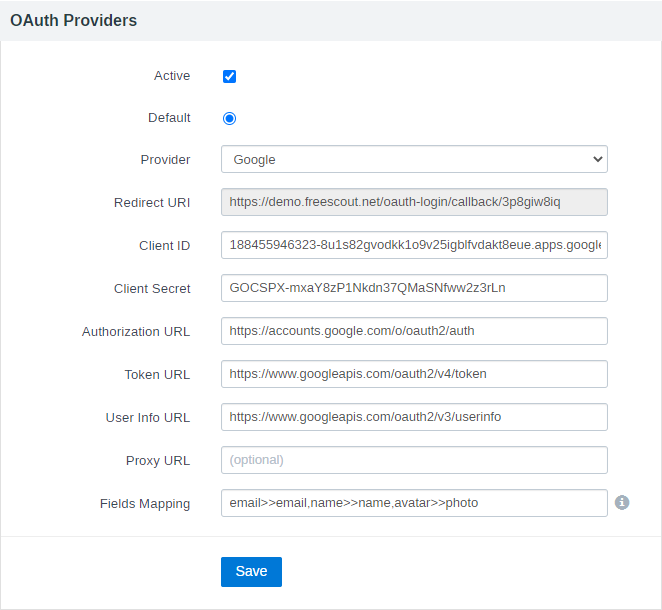
The module already has predefined configurations for Google, Microsoft Azure, GitHub and Auth0.com.
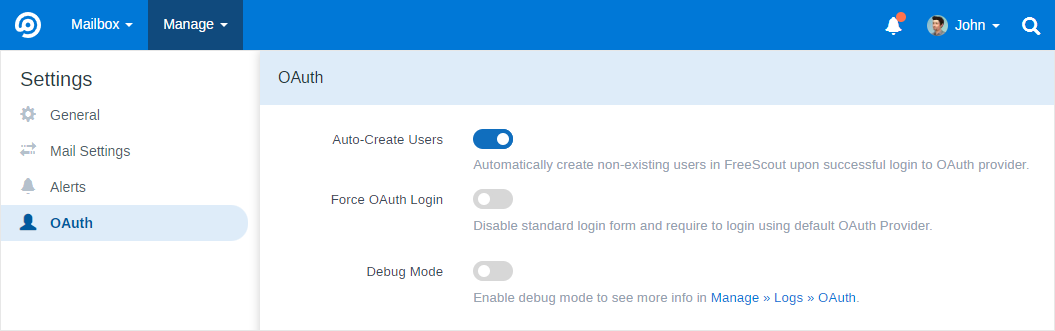
New authorized users can be created in FreeScout automatically. Also you may enforce OAuth login in the settings.
When “Force OAuth Login” option is enabled the default OAuth provider is used on Login page. If you want to allow users authenticate via several OAuth providers, disable the “Force OAuth Login” option and users will see several OAuth Sign In buttons on Login page.
If you’ve enabled “Force OAuth Login” option and can’t login via OAuth just remove “OAUTHLOGIN_FORCE_OAUTH_LOGIN=1” parameter from .env file and clear cache.
If you are using CRM Module which provides access to Customers management, users (support agents) authenticated via OAuth will also have access to Customers in your FreeScout, as all users (admins and non-admins) have access to Customers in FreeScout.
1. Create a project: https://console.developers.google.com/projectcreate
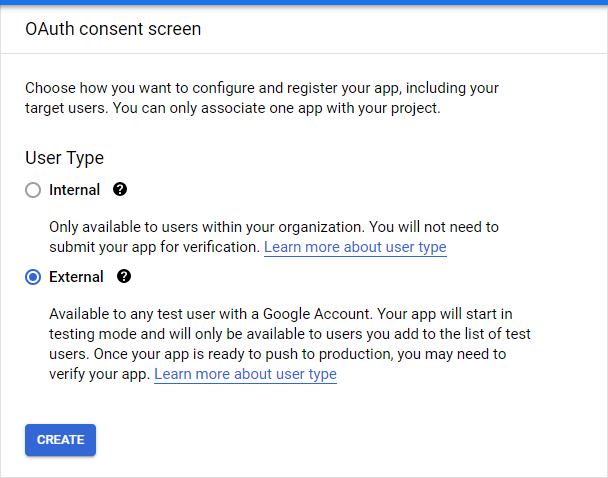
2. After that configure an OAuth consent screen.
3. Enter the following scopes when asked: openid email profile
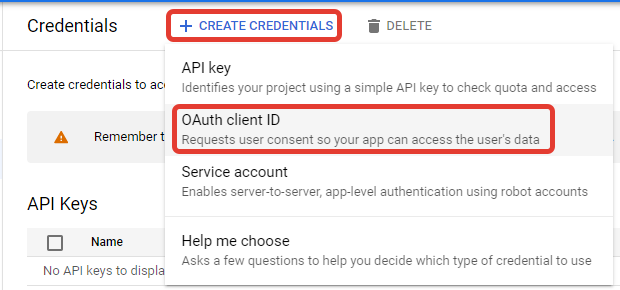
4. Create credentials: https://console.developers.google.com/apis/credentials
4. Select “Web application” as an “Application type” and enter “Authorized redirect URIs” which you can find in FreeScout for the provider.
5. A modal will pop up with your apps Client ID and Client Secret. Add these values to FreeScout.
Notice: In FreeScout mobile apps authentication via Google OAuth won’t work as Google is making some checks and asking to use some other browser. So far we could not find a solution for this issue.
GitHub
You can read here how to create a GitHub app.
Keep in mind that this is the general OAuth authentication plugin and it will not allow to adjust users access based on user’s GitHub organization.
Microsoft Azure
We don’t have yet an instruction on how to configure oAuth on Microsfot Azure’s side.
Here are some options which you can append to the “Authorization URL”: https://login.microsoftonline.com/{tenant-id}/oauth2/v2.0/authorize?prompt=select_account?parameter1=value1¶meter2=value2
For example if you want to force account selection for Azure user upon login (instead of automatically logging in to last used use) add “prompt” parameter to the “Authorization URL”: https://login.microsoftonline.com/{tenant-id}/oauth2/v2.0/authorize?prompt=select_account?prompt=select_account